LinkedIn’s notorious 2012 data breach came back to haunt it last week, as 117 million more email and password combinations appeared for sale on the dark web, a massive addition to the 6.5 million made available in the wake of the original breach.
Many of us would do well to take this development as the latest reminder that, if it can happen to a company as digitally diligent as LinkedIn, it can happen to anyone.
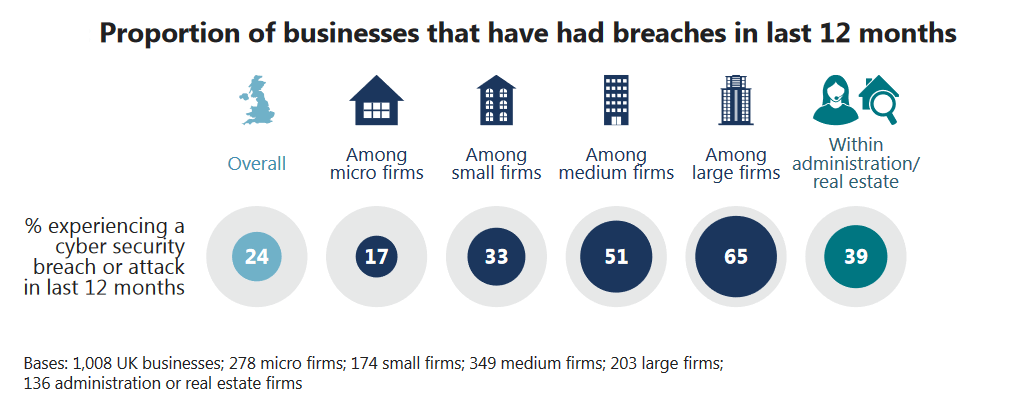
Indeed, according to new research published this month by the UK government, The Cyber Security Breaches Survey 2016, a jaw-dropping 65% of large UK firms have fallen victim to a cyber security breach or attack in the past year, while 25% reported experiencing a breach of some kind on a monthly basis.
When you add the figures up, the numbers can look dizzying, with the average cost of a single breach to a large business being a cool £36,500. The prevailing sense, in the UK and elsewhere, is that the scale and expense of cybercrime demands a collective, organized response.
Source: The Cyber Security Breaches Survey 2016
For its part, The Cyber Security Breaches Survey 2016 would have employers invest a lot more in training programs that seek to inspire more responsible digital behavior, making much of the fact that only 17% of UK firms presently provide training of any sort in this area.
However, while much more could certainly be done to engender more responsible behavior in end users, the fact remains that, as long as your enterprise is dependent on end users to keep it secure then… it won’t be.
Human error, of one sort or another, is simply inevitable.
Enter Windows 10
This is what excites so many analysts about the Windows 10 security features. It isn’t only that they represent a new benchmark in security (though they do this, too), but that the interlinking new features Device Guard, Credential Guard and Secure Boot turn the traditional approach to enterprise IT security on its head.
In a nut shell, Windows 10 allows the enterprise to move from a ‘blacklisting’ approach to detecting hostile programs (banning known-bad code), to a ‘whitelisting’ approach (only known-safe programs are run). The theory is that, with Windows 10 in place, humans can err all they want, but unauthorized programs simply cannot be run.
To achieve this state, however, it is vital that Windows 10 is properly installed.
For example, Windows 10 security feature Secure Boot (a vital component of the overall suite) requires Unified Extensible Firmware Interface with a GUID Partition Table disk configuration. While devices have been manufactured with UEFI for several years, unless they were supplied with Windows 8/8.1 installed it is very likely that they will be running in a BIOS emulation mode with a Master Boot Record (MBR) disk configuration.
What that means is, for many businesses, especially those presently running Windows 7, an in-place upgrade will prevent them from achieving a fully secure Windows 10.
[vimeo_video id="165417605″]
So, if security is important to you – you not only need to get to Windows 10: you need to think about how you get there.
A new 1E webinar series, Windows 10 – Get a True Sense of Security for the Enterprise, kicked off on June 8. Watch the first installment on-demand now!




