There’s one positive thing that comes out of hacking: information.
This information can help your business protect itself from potential intruders looking to exploit the loophole and extract secure data.
If you’ve ever seen the movie Hackers, you’ll recall punk kids trying to infiltrate systems. They wanted to change their grades, hack ATMs for spare cash, and change the criminal records of their teachers. Mostly it was just for a laugh, to prove that they could do it. There wasn’t any real harm done. Plus, it was a movie.
Though clearly, this type of hacking is unethical. This form of hacking, often called Black Hat hacking, is done for personal gain. We recently spoke about Jackpotting. If you recall, it's a cyber attack which stems from hacking ATM machines to steal money directly from the bank and not the machine itself. This is just one example of a series of hacks that are corrupt.
There are some types of hacking that are actually good for you.
This is called White Hat hacking. White Hat hacking is done to find specific vulnerabilities within an IT system. This helps protect it from potential Black Hat hackers.
After a team does some White Hat hacking within a system and patched the vulnerabilities, sometimes the business will do a penetration test.
Penetration testing (pen testing for short) is basically a controlled cyberattack. It's performed either internally by your security team or by a third-party in an effort to highlight vulnerabilities within your business. Some organizations opt for a pen test for specific products before they bring them to market. Others deploy a pen test to make sure their current security tools are functioning as they should. Regardless of the reasons why the overall outcome is the star of the show. These findings help build out your security infrastructure and give your SecOps teams direction.
The goal of any business is to protect itself so that it can continuously grow.
Sometimes you follow the herd and do what everyone else is doing (ie buying the bright, shiny new tool that has no track record of actually working) but sometimes you have to break the mold to find the real answers to problems.
We asked MVP Shaun Cassells about pen testing and he said, “If you spend 5 minutes watching the news, you’ll see that there is always someone out there trying to scare you that it might all fall apart. When you are looking at businesses, you learn quickly that you are far more successful when you incorporate lots of ideas. It’s important to know that multiple perspectives can all still be correct. Business is built on being better, cheaper, faster, and being more than whatever the customer can do without you. Penetration tests are literally asking someone with a different set of perspectives to look at your business to ensure you are able to do more without someone external forcing you to do less.”
If you think of your IT estate like a house, you want to ensure the home is protected with a security system. The system doesn’t help if it’s broken or unreliable. See this image below: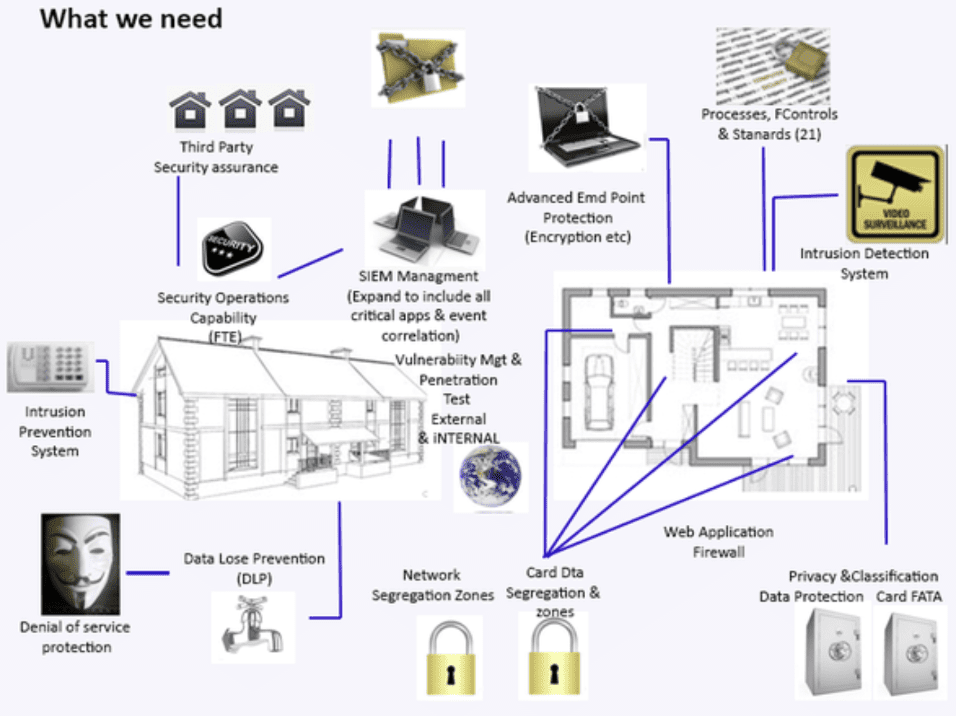
Each of these aspects of the system play their parts: from detection to remediation, the moving parts are each necessary to maintain an advanced level of security.
To protect your organization, you must first know what the weak spots are. Then you can begin to fortify them automatically, leaving your SecOps team to use resources once dedicated to older issues.




