There's a dichotomy between employee experience and endpoint security, where strict security controls will mitigate risk from cyberattacks but often inadvertently cause friction to employee productivity. The 1E Platform helps find that balance by providing employees the capability to quickly gain elevated privileges only when they need it and lock down their devices when they don't.
Organizations are moving towards an environment of least privilege to reduce their attack surface against cyberattacks. Managing local admin access is critical to achieving a secure environment to prevent access to sensitive company information. But often jobs require employees to temporarily elevate privileges to complete tasks. E.g., installing an application, gaining USB access for presentations, adding a printer post PrintNightmare, etc.
1E Endpoint Automation rules allow IT to automatically strip all users of admin rights and provide self-service options to instantly allow access only when the employees need it (typically for 5 to 15 minutes). The platform's real-time nature allows users to get their job done within minutes and automatically de-elevates privileges seamlessly in the background after their allotted time has expired. This allows security teams to maintain compliance without requiring a flood of service desk tickets to manage admin privileges.
Use case
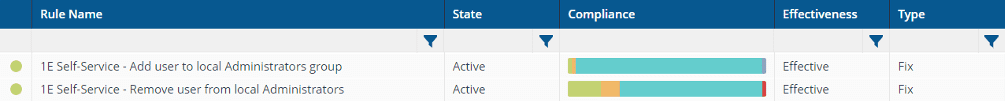
You can deploy 1E Endpoint Automation rules to every device in the organization to automatically manage admin access. The first rule below provides self-service capabilities for the employee to elevate privileges on demand for 15 minutes (time is configurable). The second rule below automatically removes the user from the local admin group as soon as the 15 minutes have elapsed.
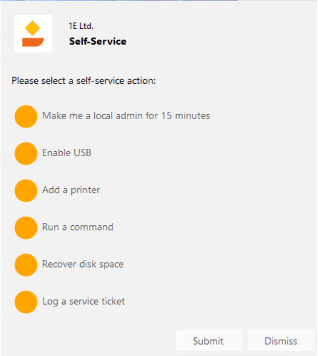
The Endpoint Automations are ready to jump into action as soon as an employee makes a request through the self-service pop-up notification on their device. This can be opened at any time with an icon on the desktop, as shown below.
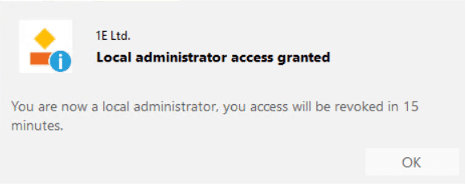
For cases where an employee may want to install a new application, they can select the "Make me a local admin for 15 minutes" option above. This instantly adds the user to the local admin group to allow them to complete their task.
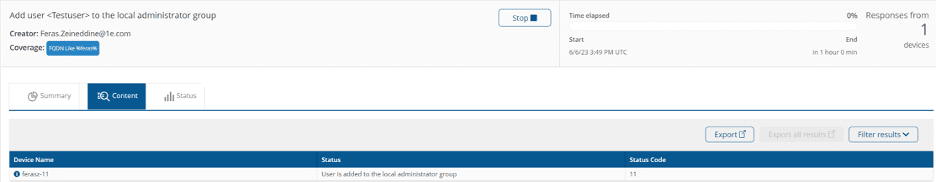
1E Endpoint Troubleshooting instructions can be used by the service desk or IT operations teams to gain elevated access to specified devices in real-time. This is critical to quickly resolve tickets remotely by providing the service desk with admin privileges to run a script—or other troubleshooting methods—without requiring a Remote Desktop Protocol (RDP) session.
If an RDP session is required, the same methodology can be used to lock down RDP access and only enable it when needed, as shown below.
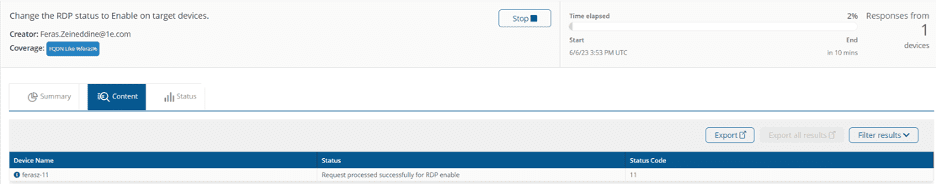
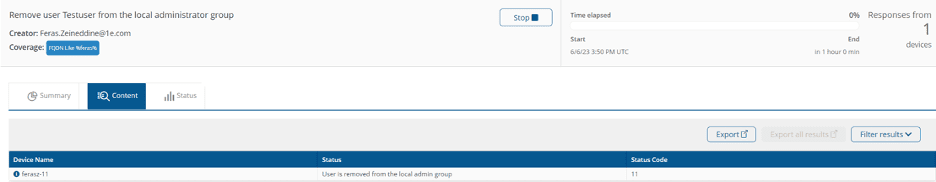
Once the ticket is resolved, the user can be removed from the local admin group on demand.
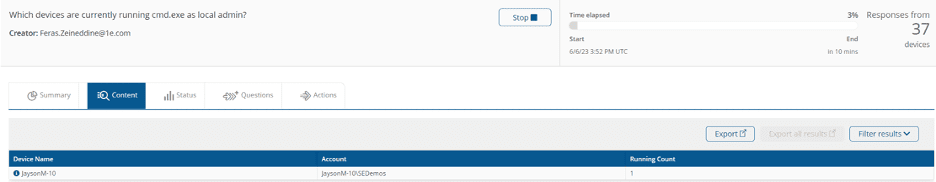
Lastly, the ability to see which processes are running as admin provides IT with the insight to make data-driven decisions on which applications require admin elevation or not. It's often found that legacy applications that are critical to day-to-day operations require elevated privileges to run correctly, which requires custom controls to keep the devices secure without impacting the performance of the app.
Tips and tricks
The real-time nature of the 1E Platform not only provides instant access to data and configurations on all devices in the environment but also the ability to remotely make changes to the device as if you were sitting on the command line.
Managing privileged access is the first step to reducing the risk of attacks. 1E takes it one step further in providing the ability to quickly respond to security threats if bad actors do make it through security control. The out-of-the-box functionality of the 1E Platform makes identifying impacted devices, quarantining them, and enacting the necessary changes to eliminate threats possible.
Conclusion
Taking control of access management reduces your organization's security attack surface by a significant amount. Verizon's 2022 data breach investigations report found that 82% of breaches involved the human element. Whether it is using stolen credentials, phishing, misuse, or simply an error, people continue to play a very large role in incidents and breaches alike. Revoking privileged accounts and administrative protocols, such as RDP access, and temporarily provisioning access—only when required—provides the balance between a secure environment and a great employee experience.




