Even the best prepared IT team can’t plan for a zero-day vulnerability; So, what do you do when faced with an immediate risk to your environment’s security?
Do you configure SCCM or Intune to push required updates and wait for those updates to eventually reach your fleet?
Send an email out to your users asking them to take manual steps to remediate the issue?
If you are a 1E Tachyon customer, you can patch potential holes in your environment’s security in seconds. We’ll be using last week’s Chrome zero-day bug CVE-2022-2856 as our example.
CVE-2022-2856 is described as “Insufficient validation of untrusted input in Intents.” An Intent in this case refers to a mechanism which triggers an application directly from a website, which then feeds the data on the site into the external app. This could potentially allow bad actors access to your system’s data.
Thankfully, the fix is easy – you need to update Chrome. This would not be a problem on your personal device but at enterprise scale this can become a time-consuming, extraordinarily messy job. Unless you’re using Tachyon…
Here’s what we did: We downloaded this instruction from the Tachyon Exchange, uploaded it to our environment and clicked ‘Perform this Action’ and in under a minute, hundreds of successful updates were reported back to us. Let’s see SCCM or Intune do that.
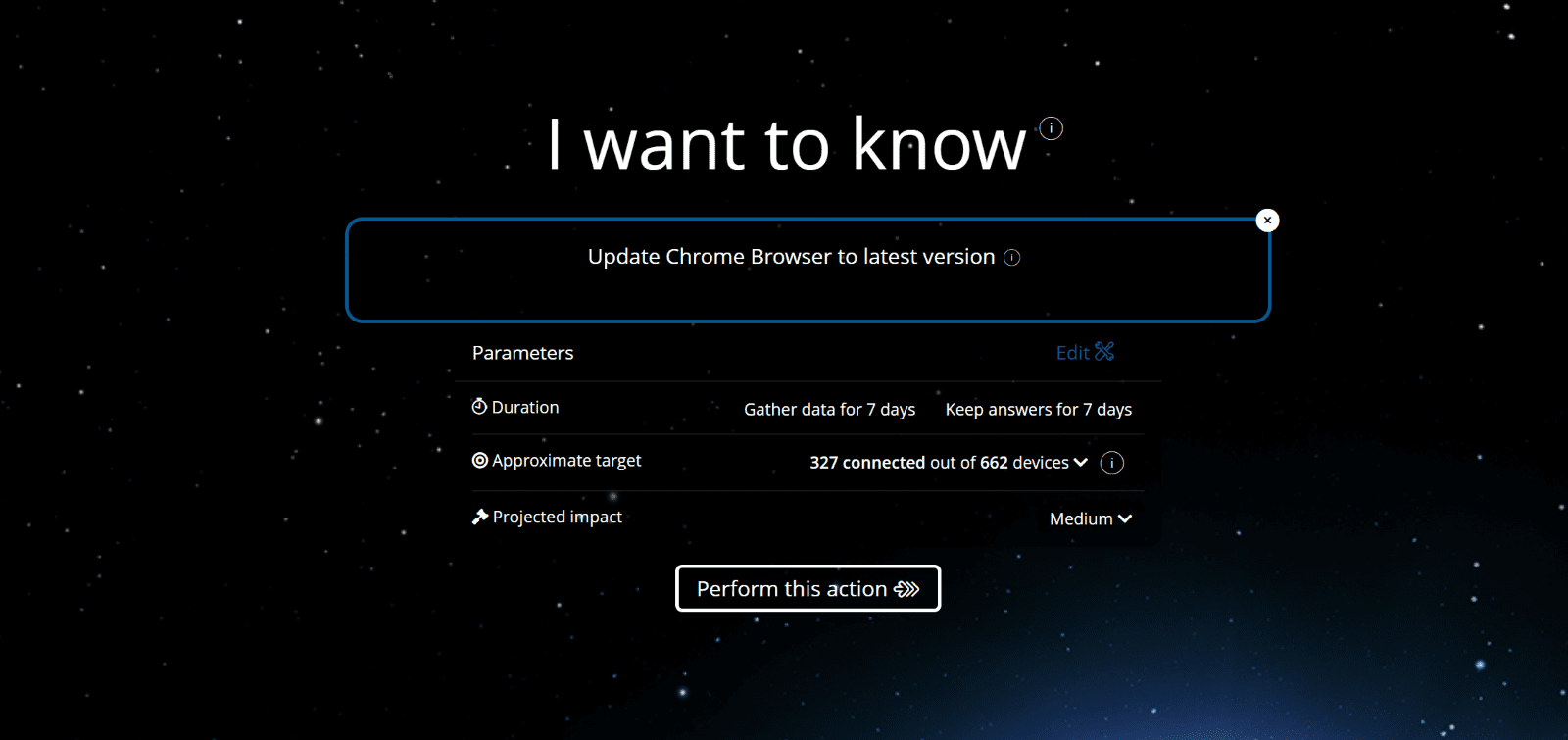
This instruction downloads the most recent version of Chrome directly from google and will work without being updated for each new version of the browser. Saving your team time and effort in configuring new updates.
If you want to learn more about Tachyon, why not take a look at this prior blog series for insights, tips, and tricks!




