It is undeniable that business risks associated with security breaches are accelerating. Hardly a week goes by without the media reporting a major breach at a large company or government institution expected to employ only the highest of security protocols. Endpoints pose the biggest risk to organizations because this is where most vulnerabilities are exploited. As a result, the endpoint is rapidly becoming the center of the universe for security and operations teams, and thus crucial to improving overall cybersecurity posture.
For endpoints to be managed and secure (which ensures productive users), it’s paramount that endpoints are actually visible and within reach of IT and security teams. In spite of this, IT managers agree that achieving security requirements is the leading challenge to endpoint management. Endpoint management practices are the most time-consuming, difficult, costly, and disruptive to end-user productivity. Even more problematic, many popular tools being used to automate Endpoint Detection and Remediation (EDR) are actually not capable of providing the kind of pervasive visibility required to manage the entire IT estate effectively.
Visibility of all endpoints has become a real challenge due to an increased reliance on distributed endpoint devices that are permitted to be utilized both inside and outside of secure network environments. Rather than being tethered to an office PC, employees regularly use a variety of different endpoint devices to access business systems and IT services from home or other remote locations. This substantially increases their vulnerability. Secondly, enterprise applications, data, email, and other services are now broadly hosted across internal and external server as well as cloud environments. In fact, the distribution of software-as-a-service (SaaS) applications and web applications have now exceeded the use of downloadable applications in business environments, further decreasing the control and visibility organizations have over their IT resources. The net result of the mobile and cloud revolutions is that it created device “blind spots” for most IT and security teams.
EDR tools are designed to provide the visibility and automation required to investigate and respond to endpoint threats in real-time. These platforms continuously monitor and record the status and events on supported endpoint devices. Ideally, an EDR solution should monitor and support all endpoint devices employed in an organization, regardless of location. However, the “consumerization of IT” over the past decade granted end users greater freedom in selecting the devices they wish to use to perform job tasks and where they do so. As a result, there is now a much greater variety of enterprise supported devices than ever before, and organizations supporting a wide range of operating system editions and versions will need an endpoint detection and response solution that can consolidate multi-device support onto a single console. Independent industry analysts EMA, recently evaluated two leading EDR solutions, 1E Tachyon and Tanium, to take a deeper look into their respective coverage of supported platforms.
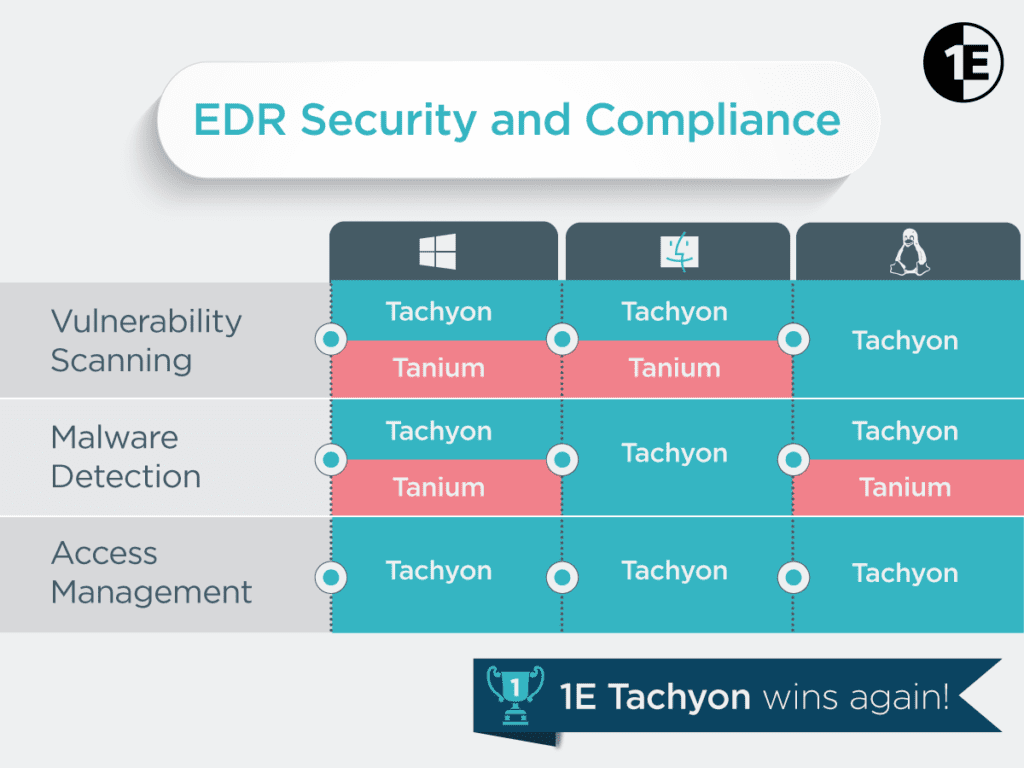
Microsoft Windows still dominates the enterprise PC market, and most EDR solutions provide good support for Windows endpoints. This is certainly the case with Tanium and 1E Tachyon, both of which provide broad support for the common editions of Windows in use today. However, Tanium has discontinued support for legacy OS editions, including Windows XP and Windows Server 2003. Tachyon, therefore, will likely find a welcome audience in those organizations that still employ older Windows versions to support custom-built applications for those environments. Similarly, both platforms provide support for Apple Mac OS X endpoints, but, again, Tachyon provides support for older editions of the operating system as well.
The clearest differentiation in platform support can be seen with mobile devices. Since the peer-to-peer (P2P) architecture employed by Tanium is only effective on static devices that are continuously fixed to a particular LAN, the solution is not designed to monitor and manage mobile devices that move from location to location. As a result, Tanium has no capabilities for extending the platform to supporting smartphones, tablets, or any other portable devices. Thanks to Tachyon’s one-to-one connection architecture, 1E has been able to introduce broad support for mobile and other types of devices. The one noticeable absence is support for Apple iOS devices. However, 1E has reported to EMA that an iOS agent is currently in development and will be introduced shortly.
The recent evaluation by EMA of the platform support offered by both EDR solutions revealed nearly all reported functionality was supported on Windows and Mac endpoints, but somewhat fewer capabilities were enabled for Linux and UNIX systems. While both solutions support a number of Linux versions, 1E Tachyon extends support to a broader range with included support for Debian and Fedora Linux editions. For UNIX support, both solutions can manage Oracle Solaris endpoints, but Tanium Core is also able to extend support to IBM AIX.
The core purpose of introducing an endpoint detection and response solution is to ensure and report on the security of end user computing resources. In order to be effective, these tools need to support the platforms your end users are using today. The only alternative is accepting the risk of blind spots in your security investigation and remediation processes. You simply can’t manage what you can’t see.




