Like many IT professionals of a certain vintage, I'm pretty sure I have been subconsciously conditioned over the years to associate the word ‘Tuesday’ with the word ‘Patch’. Accordingly, when I had the opportunity to pen a guest blog post for Tachyon Tuesday, just like Pavlov’s Dog, my classical conditioning had already predetermined the theme – it was always going to be about patching combined with automation. With coincidental timing, it has been precisely 7 days since Microsoft issued CVE-2021-34527 – relating to a particularly nasty remote code execution vulnerability with the Windows Print Spooler service aka PrintNightmare.
So, what is this vulnerability, how does it work, and how can I defend my enterprise IT environment from being compromised? Let’s start with the Windows Print Spooler service itself.
The Print Spooler service is a key operating system component on every Windows PC that manages all printing on the device. It starts itself up when you boot your PC and runs silently in the background with no systems tray icon or UI for users to interact with, waiting and listening for any application on the computer to send through a file – or multiple concurrent files – for printing. Every PC has it as a core part of its OS, so it’s the perfect vector for malicious actors to target as many potential victims as possible.
The problem for Microsoft, and by extension every corporate and private user of a PC, is that back in May cyber security researchers published details on how hackers could subvert this ubiquitous service. In fact, a skilled hacker could use it to remotely view data, install applications, and even create admin accounts on their victims’ devices – starting with Window 7, and right up to Windows 10 and 11. With all the recent high profile cyber-attacks against organizations, ranging from oil and gas pipeline providers to entire health-care systems, the last thing enterprises need is yet another potential avenue of attack for cyber criminals.
The Resolution
The Microsoft Security Response Center (MSRC) has posted detailed, clear steps and guidance for organizations to take which mitigate the risk associated with this critical vulnerability. It is notable the extraordinarily high CVSS score of 8.8 assigned to this CVE – which speaks to the damage that a skilled hacker could wreak using its SYSTEM level code execution abilities.
To prevent the possibility of compromise, the MSRC recommend a multi-phase approach:
- Apply latest security updates, noting that all updates released after July 6th have the protections for CVE-2021-1675 and CVE-2021-34527 (PrintNightmare)
- Verify the following registry settings are ALL set to 0 on ALL devices:
-
- HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\Printers\PointAndPrint
- NoWarningNoElevationOnInstall = 0 (DWORD) or not defined (default setting)
- UpdatePromptSettings = 0 (DWORD) or not defined (default setting)
- Verify the GPO settings are valid and correct
The workarounds suggested are seemingly similarly straight-forward:
- Disable the Print Spooler Service – though this removes the ability to print locally or remotely
- Disable inbound remote printing (still allows for local printing)
Of course, there is often a significant gap between knowing the steps that must be taken and being in a position to verify positively that those steps have taken effect. Too often the legacy paradigm for systems management and vulnerability response is that of set remediation policy and wait for it to apply pervasively.
Tachyon Instructions to Instantly Diagnose and Remediate
1E customers around the globe were able to effectively respond to PrintNightmare using Tachyon’s ability to interrogate end-points and make instant settings changes in real-time.
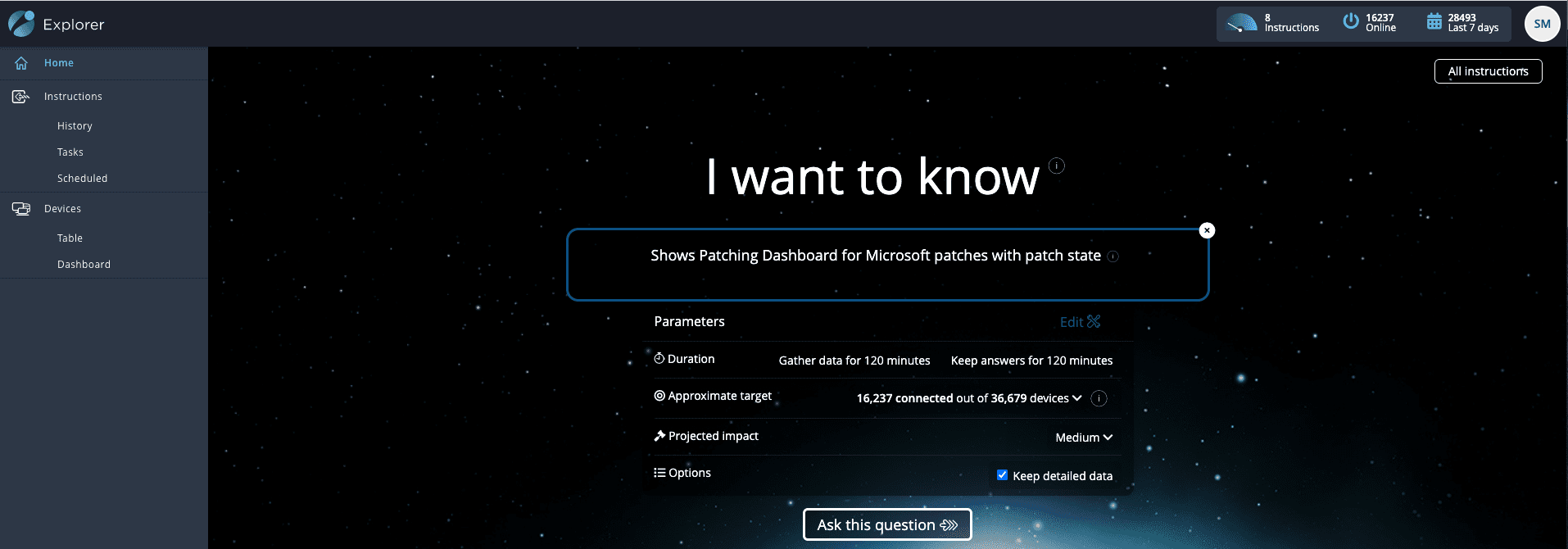
The first thing Tachyon can verify for us is exactly when every single device in the environment was last updated, and if we have any that still need to be remediated. We can gather that information instantaneously using one of the pre-built Tachyon instructions. Here I am asking 16k online devices for their current patch state:
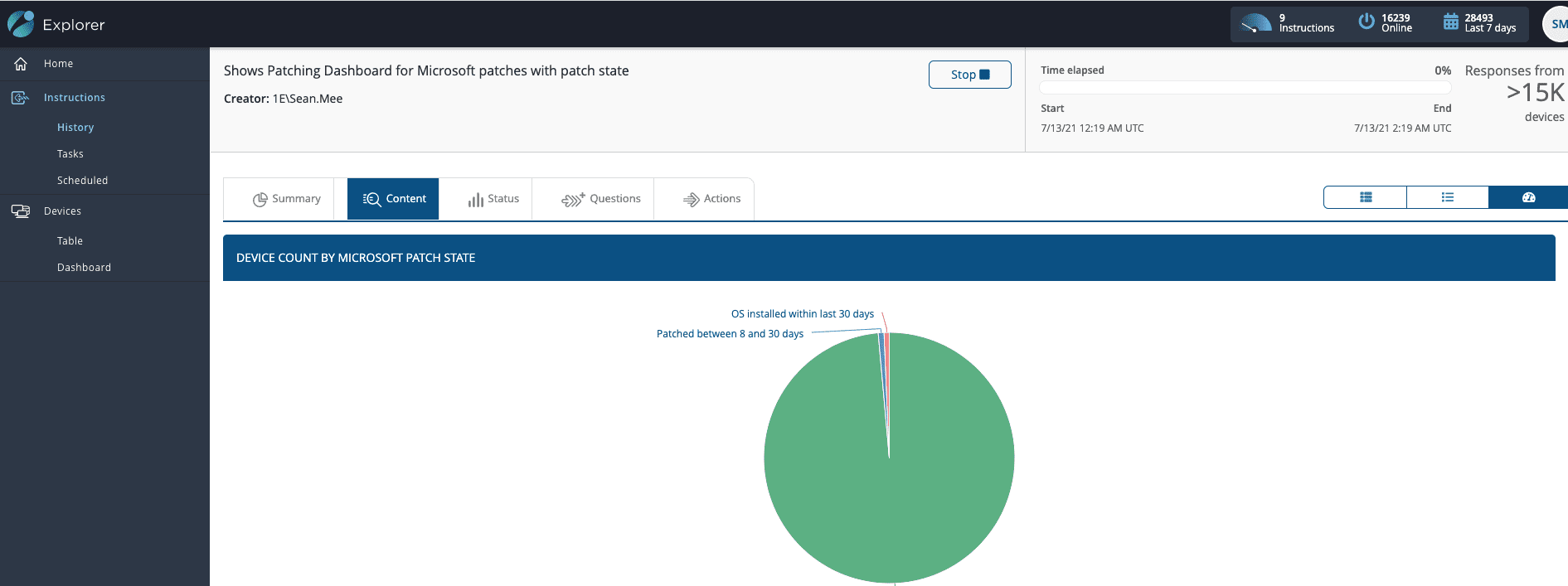
Within a second or two, I can straight away verify which machines need an update – already reducing my search space and scope as part of the resolution process.
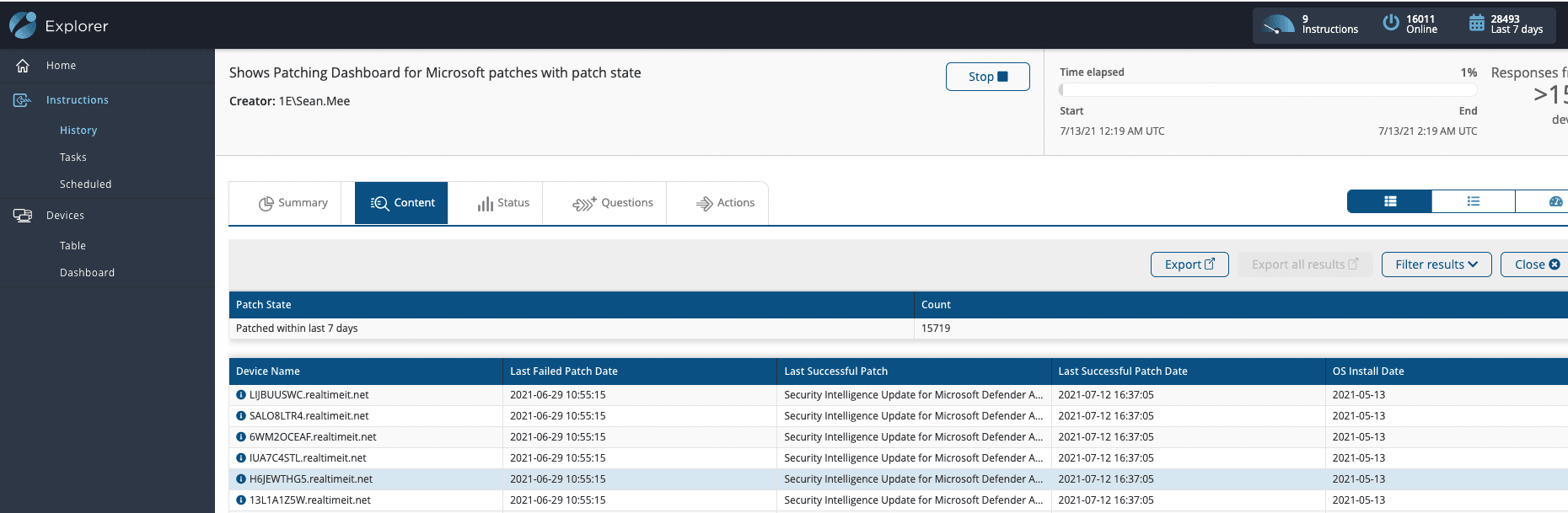
By this stage, I am about a minute into my investigation and can clearly see if any devices haven’t been updated since last Tuesday.
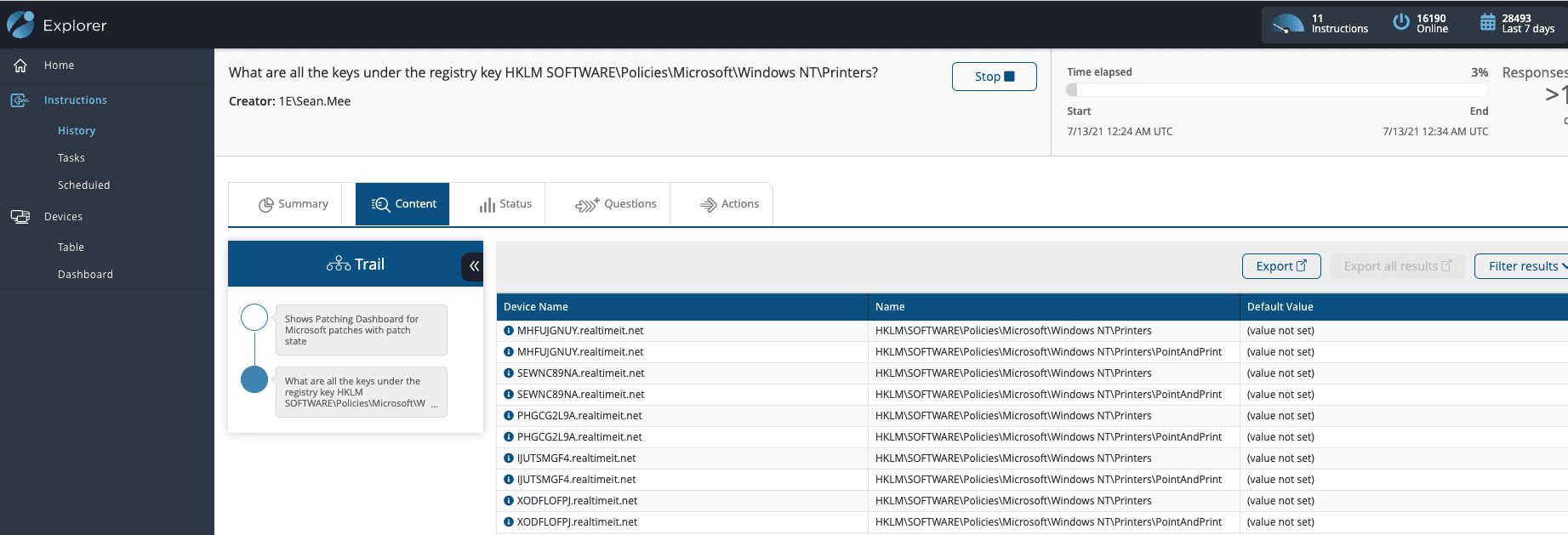
Next up, I will want to verify those registry settings – after all, even with the patch applied, we are still not protected until we ensure those settings are correct. Once again, Tachyon allows us to simply ask a ‘Follow-on Question’ to see which machines need a registry setting change. Within seconds of identifying the patched systems, I can also parse out the registry values defined by MSRC to be of interest:
And of course, we can issue a ‘Follow-on Action’ to update the registry setting to a 0 if required, again from within the same investigative workflow within Tachyon:
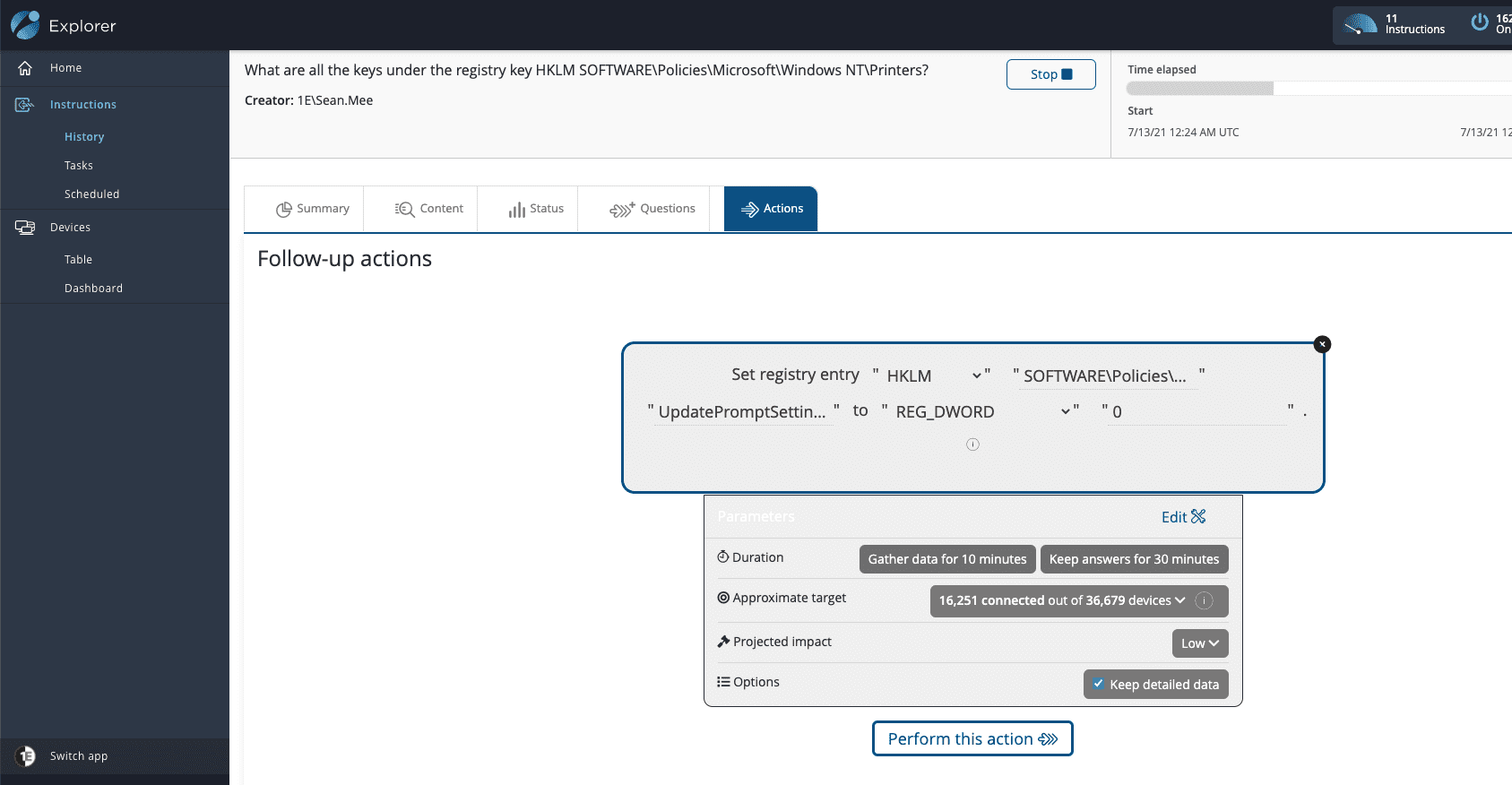
So, there you have it – instant visibility into affected systems, with the capability to remediate them all in a single console in real-time – not bad for a morning’s work and all possible out-of-the-box for users of the Tachyon platform.
If you found this Tachyon Tuesday vlog helpful, why not check out other editions of Tachyon Tuesday? Or subscribe to our YouTube channel to stay up to date with the latest Tachyon Tuesday content!




