On December 9th 2021, Log4j or Log4Shell, a critical new zero-day vulnerability (CVE-2021-44228), was publicly released. The security vulnerability was found in Apache's Log4J component which is commonly used in Java products for logging. The vulnerability utilises the JNDI feature to cause malicious code to be downloaded and executed on a remote server.
What is the Log4j vulnerability?
Put simply, the Log4j vulnerability allows attackers to remotely control and execute code on vulnerable machines. As Marcus Hutchins, noted security researcher, explains ‘millions of applications use Log4j for logging, and all the attacker needs to do is get the app to log a special string’. This gives hackers the ability to import malware to completely compromise machines, leaving many at risk.
https://twitter.com/MalwareTechBlog/status/1469289471463944198?s=20
Why does it matter?
The Log4j exploit could allow hackers access to your computer systems, permitting them to install malware, steal user credentials, and more. Cybersecurity researchers at Check Point have warned that there are over 100 attempts to exploit the vulnerability every minute. Similarly, Sophos has warned they’ve detected hundreds of attempts to remotely execute code via this vulnerability since last week. The proof is there that this is not only a severe concern, but it is also being actively exploited and affecting everyone from Minecraft to Steam and beyond. No one is exempt.
How can 1E help?
It’s vital that organizations protect themselves ASAP, and advice from the likes of VMware and Kaspersky is to patch and scan your environment, monitor for abnormal traffic flow and unauthorized configuration changes, and install the most recent version of Log4j library.
One of the biggest challenges organizations face is understanding if they are impacted by a vulnerability. Tachyon can be used to help identify if your organization has been impacted by CVE-2021-44228. By using the Tachyon Explorer application, you can simply ask the entire endpoint environment if they have any log4j.jar files on disk and get a response in a matter of seconds, regardless of the number of endpoints being queried, due to Tachyon’s unique distributed computing framework.
1E fast search technology will be able to search the complete disk drive in seconds without impacting the employee.
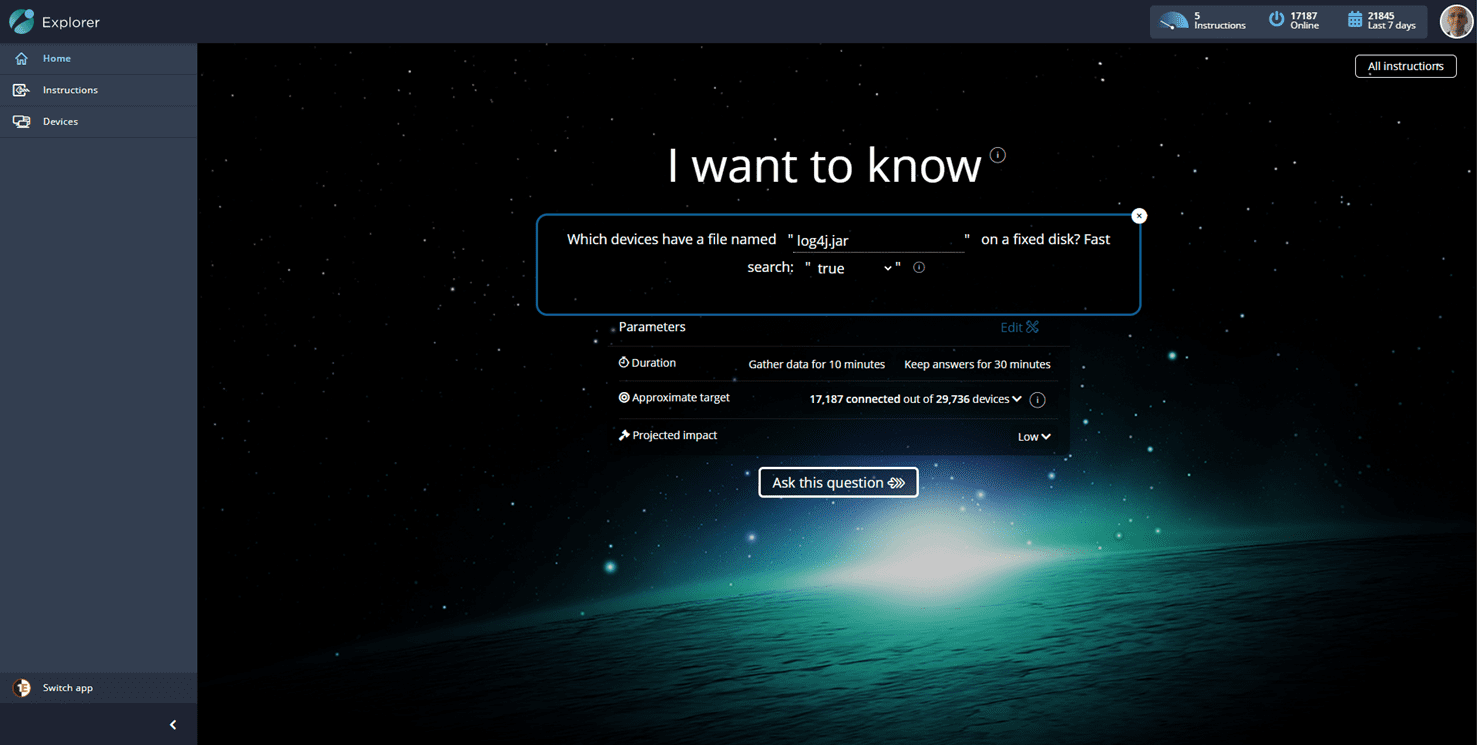
This instruction provides details about Apache Log4j2 jar files, including the directory path, size, and hash. Not all instances found from this instruction should be considered vulnerable. However, the results can help identify which systems and file locations that are potential targets for mitigation or should be investigated further.
Be sure to bookmark this page as we’ll have something special to support you in implementing your own fix soon – watch this space! In the meantime, why not get in touch to learn more about Tachyon and how it can help your organization in understanding potential vulnerabilities.




