In 2003 Andy Rubin co-founded a mobile technology startup called Android. The venture centered around the ubiquitous and portable Linux operating system. Android quickly drew the attention of technology giant Google who acquired them in 2005 and to misquote William Blake, fiery the Android rose; it rapidly grabbed market share from the established and now defunct mobile platform Symbian.

Today Android now has around 81% market share with Apple trailing at 18%; they have become the only two realistic contenders in the market.
Architecturally Android has much in its favor. Back in 2010, Rubin summarized Android’s architectural advantages as a source base that is open for inspection, fast development cycles, an upgradeable security architecture and Android’s drive to blend and merge the Web and native app worlds.
But Android is not without issues, and from an IT administration perspective it presents a number of challenges:
- Unauthorized apps – There is a term in the Android world called “Sideloading”. It means the ability to install a mobile app outside of any official or approved market, such as Google PlayStore.
The technique of sideloading apps onto an Android device is relatively straightforward. I can build a new Android app and publish through my own URL in no time at all. Especially if I use a modern framework, such as ionic, aimed at Web developers and all outside of any Google approval process. I can write an app over the weekend, share it with friends, no one can stop me and that’s a good thing.
However as Sophos reported back in 2015 in their research paper “Cross-Platform Mobile Malware: Write Once, run Everywhere”, the same approach can be used to write and propagate malware:
“At SophosLabs, we have seen an increase in the number of malicious apps written with cross-platform development tools such as PhoneGap”
However, you will not hear of side loading in the Apple world because of iOS devices, such as iPhones, are intrinsically a safer environment than Android devices. As a developer, I found it impossible to install an app onto an iOS device without at the very least associating that device to an Apple developer account and using an Apple iOS deployment mechanism. Even then I certainly couldn’t make that iOS app available for download in any volume. Not without using an official Apple iOS approval and deployment mechanism.
- Bring Your Own Device – BYOD is the practice of allowing and encouraging employees to bring their own device to work. It saves the company money, plus the choice and freedom keep staff happy. Who wants two devices in their pocket, a corporate mobile, and a personal one? But BYOD can create an IT an administration and security headache, and administrators balance the privacy of the employee with the safety of corporate assets. Well-defined BYOD policies and procedures are a must and companies such as IBM propose a set of ten rules for BYOD.
As an alternative to BYOD back in 2015 Google fan-fared their “Android for Work” split personality phones. But adoption of that technology has been slow.
- Android vulnerabilities – In recent years, Google has worked hard to improve the security framework of Android. But issues remain. On 14th September Forbes reported that “Google are fighting a massive Android malware outbreak”, dubbed ExpensiveWall since it resides inside wallpaper apps. Two days earlier a new Bluetooth vulnerability called BlueBourne was highlighted by Armis; Android devices can be vulnerable in a matter of seconds.
Now you’re worried
As an IT administrator now you’re worried. Android is not without problems, but Android is very popular with your user base, and IT operations can at times be a balance between productivity and prohibition. So how do you get immediate visibility into your existing estate of Android devices?
You could employ a Mobile Device Management (MDM) solution. There are a plethora of solutions out there and although primarily aimed at corporate devices, an organization can create a set of MDM best practices and procedures for personal devices too.

Although an MDM solution will certainly improve visibility across an IT estate, they tend to lean towards historic rather than real-time data.
It’s Thursday afternoon, your boss stands over your desk with a Forbes report on Android wallpaper exploits and asks, “Are we vulnerable?” Your boss wants to know right now.
Given a landscape of regular malware and cyber attacks, we are seeing an increased customer appetite for solutions that provide an instantaneous view across an estate, not simply historical data. 1E has responded to this customer requirement with their Tachyon offering, tagged as the fastest endpoint detection and response solution.
With 1E Tachyon installed across the IT estate an IT administrator has instant visibility of endpoints. So in this particular case of Android wallpaper exploits you are able to immediately generate a couple of Tachyon questions and analyze the results:
Firstly you obtain a list of Android devices across the estate:
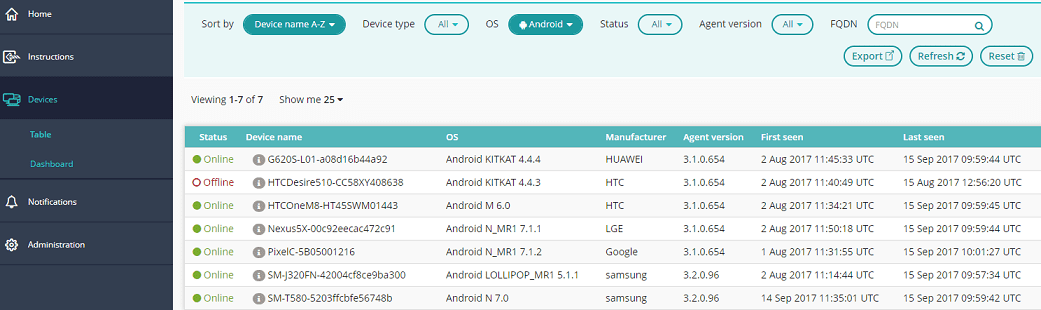
Secondly, you target only Android devices and obtain a filtered list of all endpoints with an installed app that includes the word “wall” within the product name; a simple example but a good demonstration of the power of Tachyon.
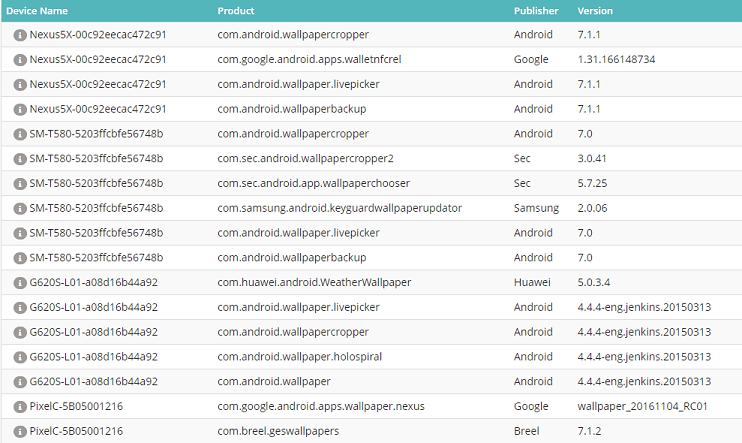
Hence you are able to immediately provide your boss with the information and assurance they need; Tachyon working with you to create a safe, productive and non-prohibitive working environment in which staff have the flexibility to use the technology that is right for them, but with the assurance of informed, agile and constantly vigilant IT administration.




