As of Tuesday, October 24th, there’s a new Cryptoware variant out there: this time, it's called BadRabbit. As the news of the malware unfolded, we immediately prepared this update for our user community which tells them how to identify and address the issue. This is another exploit leveraging similar techniques to (Not)Petya from July, so hopefully, we’re all patched up against this type of attack by now.
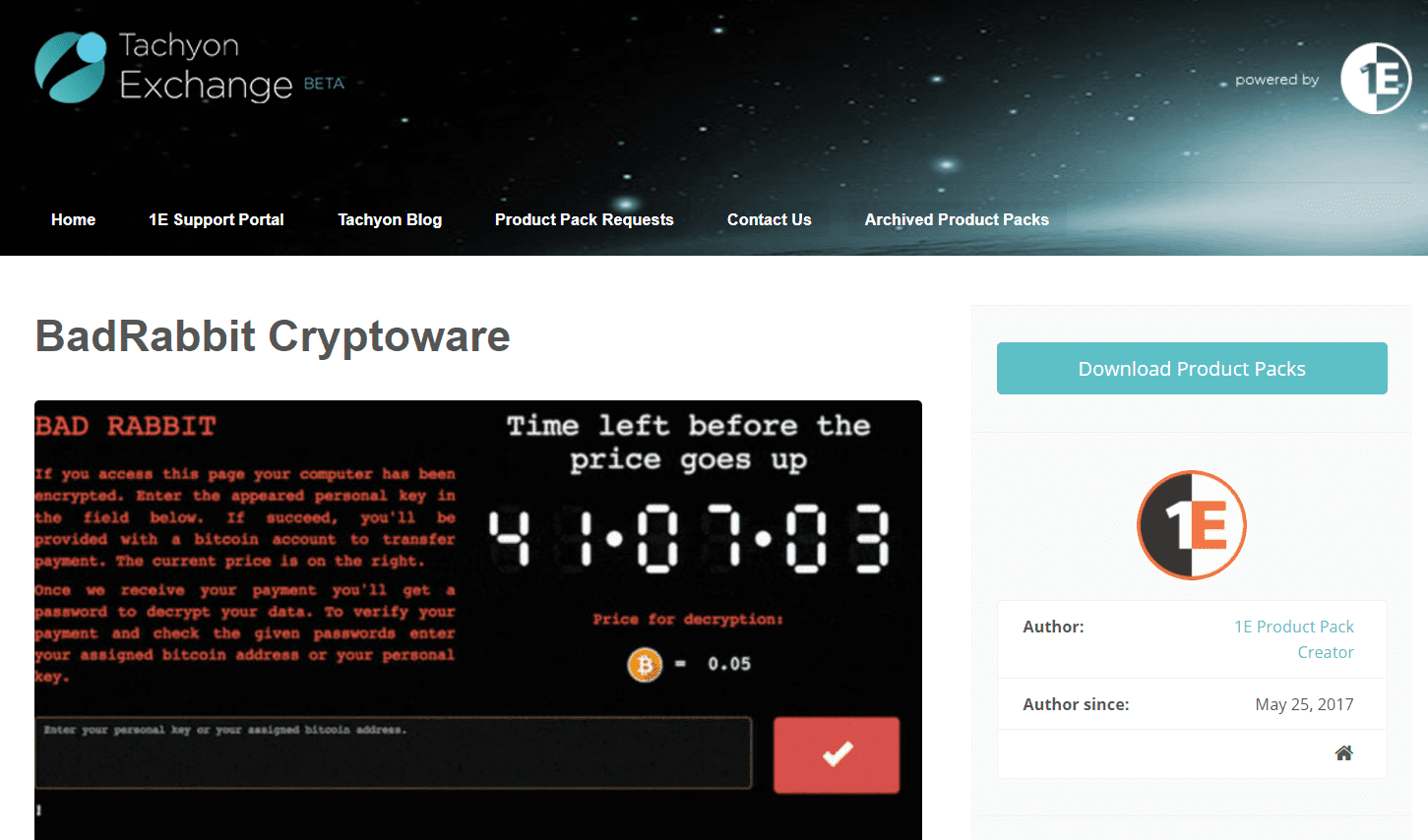
Still – it’s making headlines and you want to ensure no user has run the executable involved. Here’s how you can find and prevent this with Tachyon:
- Find any machine with a file on the disk called install_flash_player.exe
This is the file that the end user executed to have the malware start - Find any machine with a file called %WINDIR%\infpub.dat on the disk
This is the file the malware creates to get going – place an empty, read-only version of the file there to disrupt it creating the file - Find any machine with a file called %WINDIR%\dispci.exe on the disk
This is another file used by the attack. Disrupt it creating the file in advance, make it read-only - Prevent the execution of the hash for dispci.exe on your endpoints using Tachyon
8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 is the hash in question
This example showcases how Tachyon provides Endpoint Visibility, Malware Protection, and Defense.
Tachyon can perform all of the above items with existing functions, across 120,000+ endpoints in literally less than a minute. Setup the instructions to run continuously (24 hours) on a daily schedule and as each endpoint connects, it will be examined and protected against future attack from this particular malware (or any future malware using that variant of dispci.exe.)




