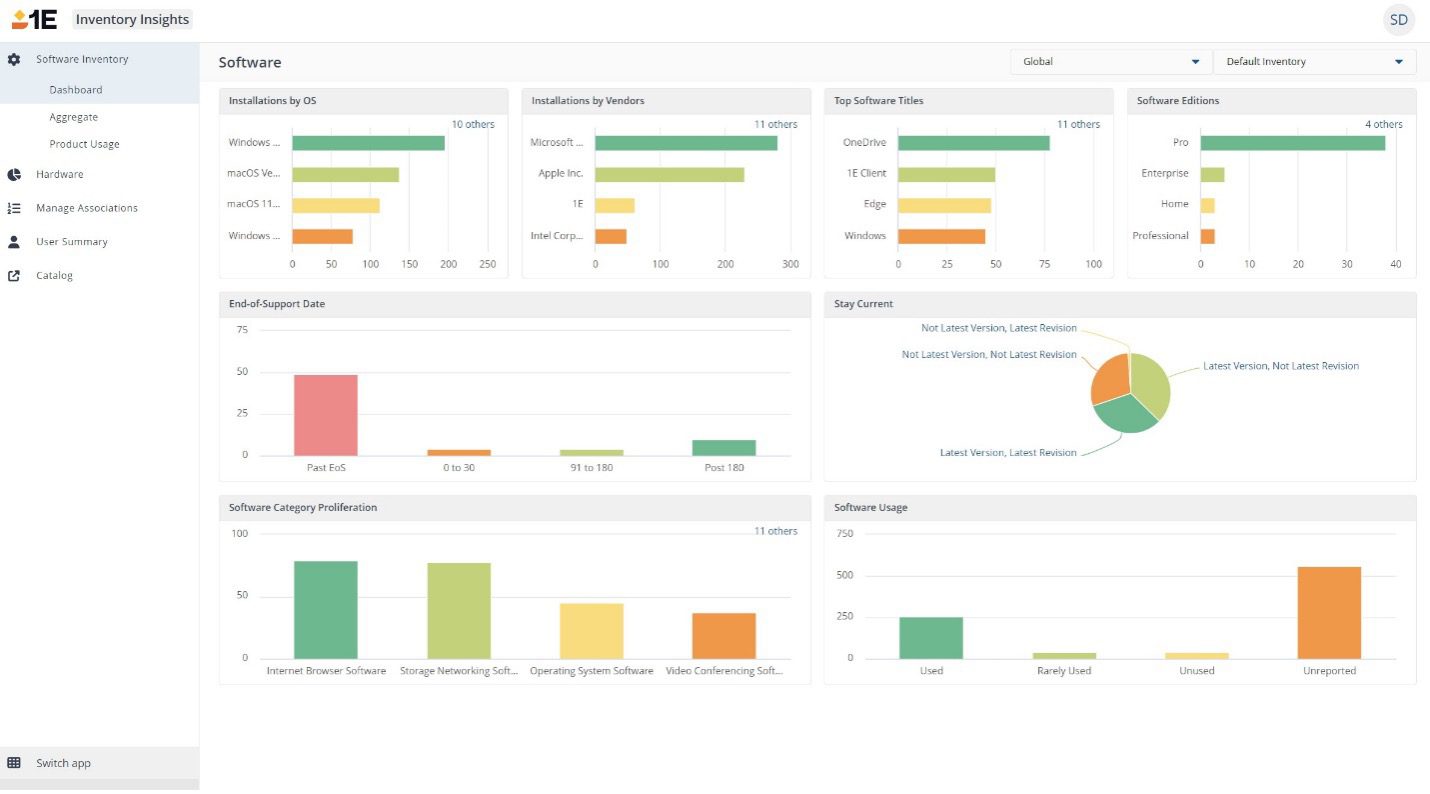
The requirements for software inventory have significantly changed over the last 5+ years. Hybrid working environments, an increase in subscription licensing, end users' expectations, and consumption of inventory data have increased IT's need for thorough inventory knowledge. Managing deployed software and having up-to-date accurate inventory data isn't only critical for Software Asset Managers, but also for security, compliance, and client engineering teams. Additionally, IT needs real-time information at their fingertips, not data that's days, weeks, or months old.
Software Asset Management (SAM) data serves as the foundation for various teams, extending its value beyond conventional software audits and vendor renewals. This data plays a crucial role in addressing security risks, such as recent instances like the Chrome zero-day threat and log4J vulnerability. Additionally, it aids in ensuring compliance and standardization, simplifying the overall environment. Finally, by uncovering shadow IT and rogue departments, organizations can tackle challenges posed by business units and regions that deploy software outside established processes.
Most enterprise organizations have thousands of applications installed in their environments. Each of the software titles deployed needs to be captured, measured, and managed. To get a single view of the software estate, IT often must combine data from multiple inventory sources (MEMCM, Intune, BigFix, ServiceNow). And, to add another dimension of complexity, the data sources often have different sync frequencies, which create conflicts in the data.
Furthermore, software like Oracle's Java can require a lot of non-standard data for risk calculation and support renewals.
Gathering software inventory data is only part of the challenge, especially when looking at data that's days, weeks, or months old. Often IT will capture this data from multiple sources over time and merge it into a single record. This increases the challenge as any inaccuracies or missing data points can instill a lack of trust in the data.
With 1E users can see and validate information against devices in real time.
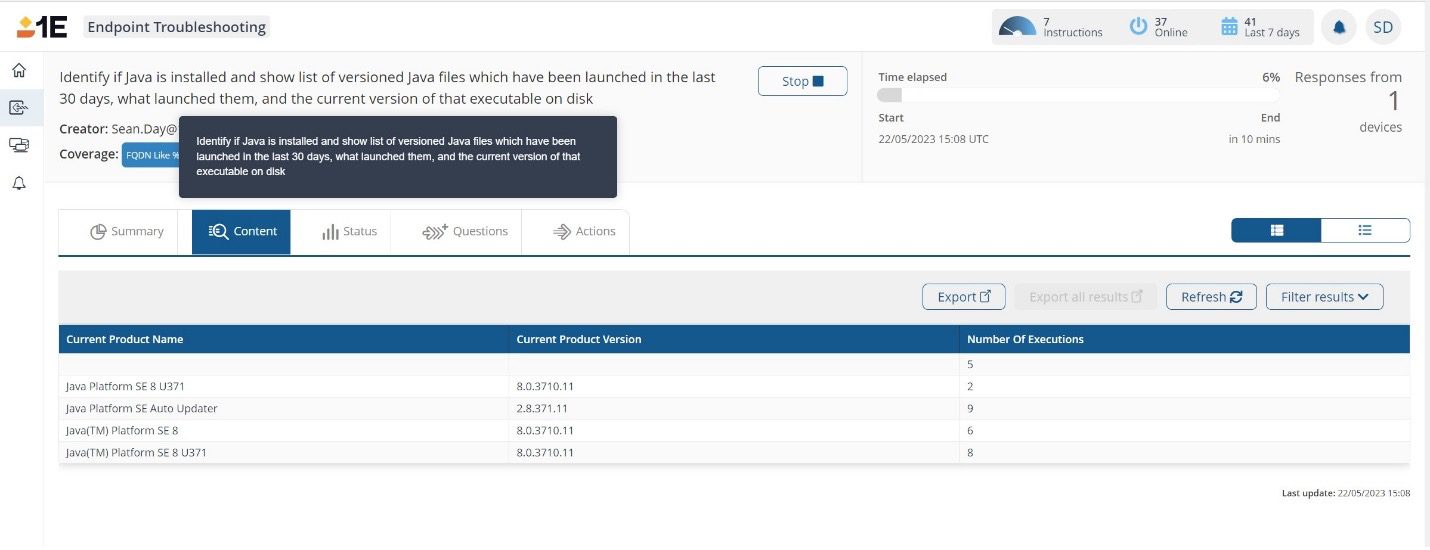
For example, when Oracle changed the licensing terms of Java, users were forced to understand what versions of Java were installed, but also if it was a component of a 3rd party application. Reviewing traditional inventory reports will provide you with only part of the picture.
1E customers have the power to accurately identify which devices have Java installed and which 3rd party applications have executed it.
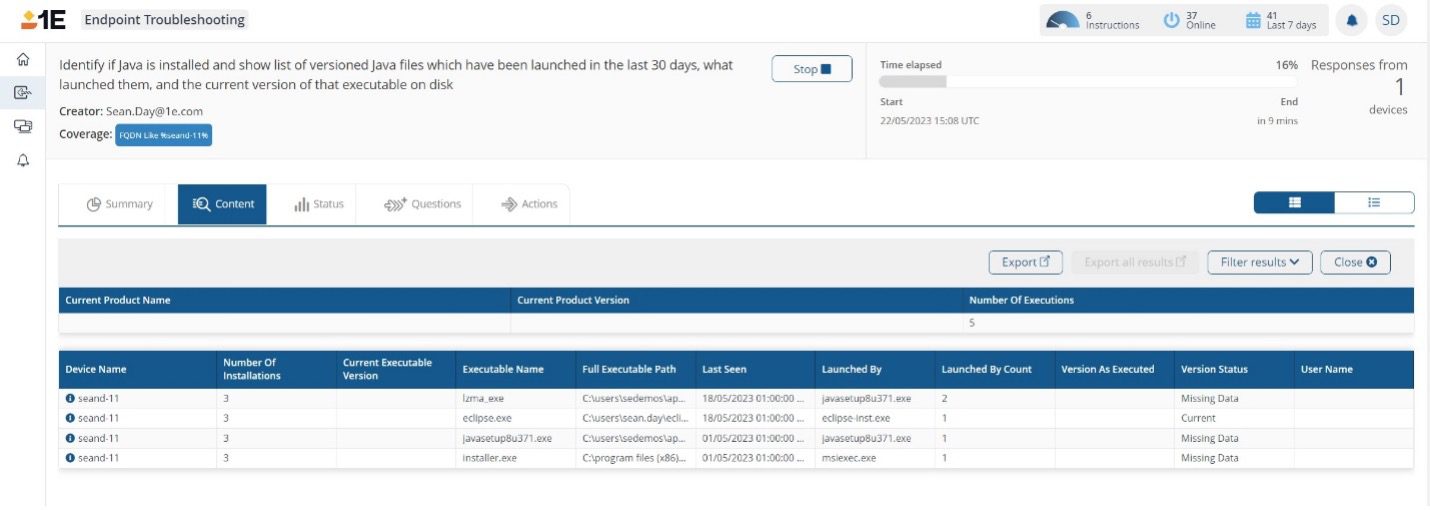
Similarly, customers have reported seeing old or removed software being continuously installed on users' machines. Traditional inventory processes can take days to validate if the cause is an outdated report, software being reinstalled, or a reporting data error.
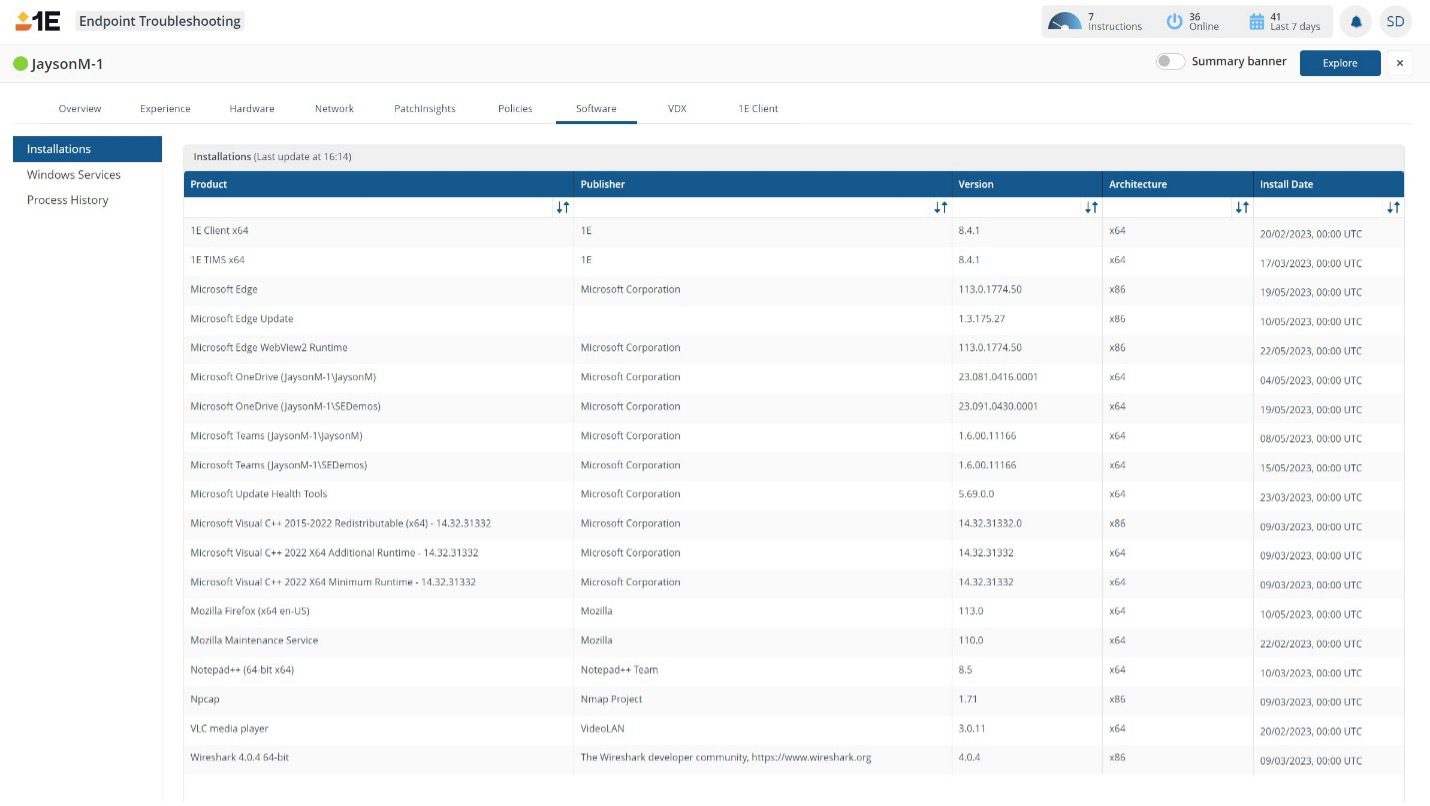
With 1E users can utilize this data to know if the software is licensable, who the primary device user is, when it was last used, and what type of software it is (based on UNSPS C categorization).
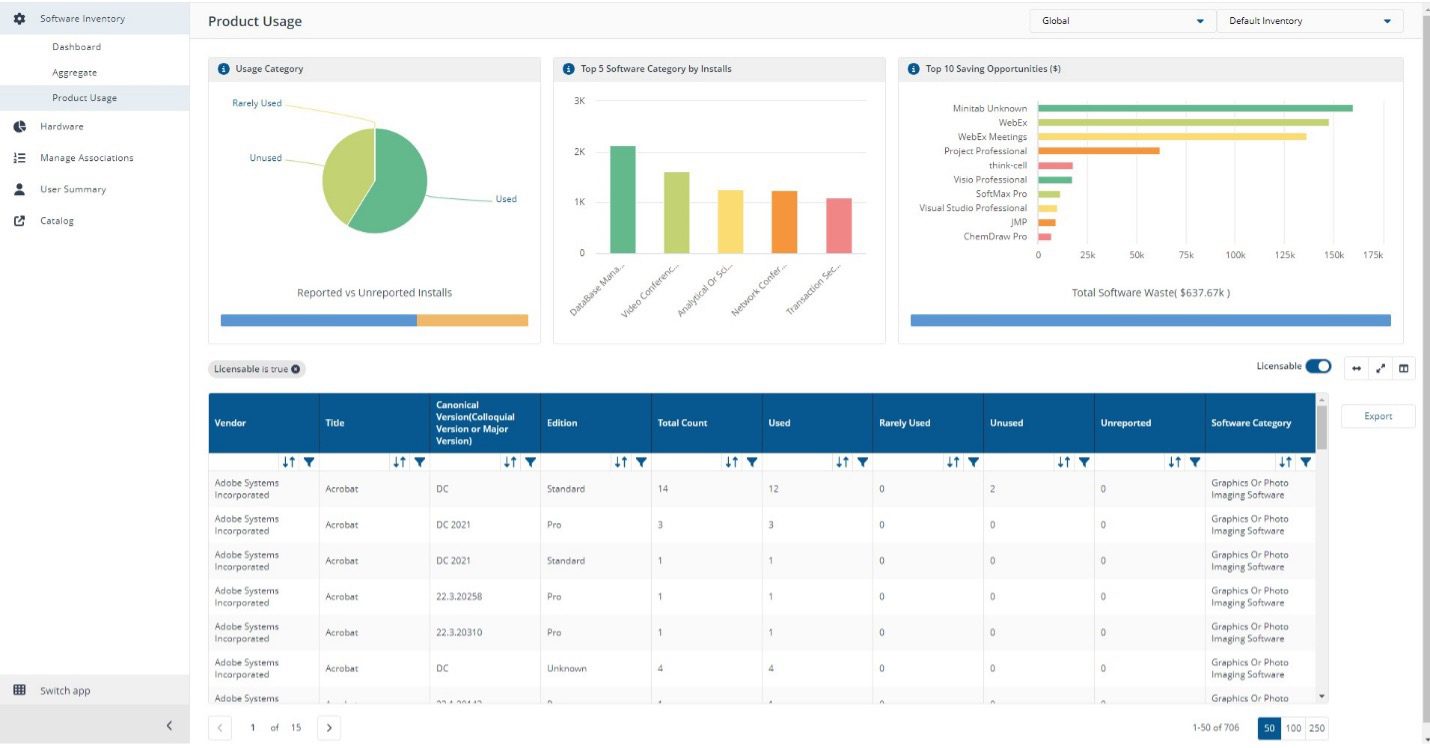
The importance of having data that's reliable and verified frees up users' cycles to focus on delivering for their organizations.
1E provides users with the ability to query any data on a device in real time. This functionality empowers users to make real impactful changes in their environments.
When Google announced its second zero-day vulnerability for Chrome, 1E users could accurately identify all versions of Chrome installed (device and user based) and upgrade to the correct supported version.
In the case of one customer, this was going from 52 different versions to 1.
Without 1E, this would involve many different teams coordinating and working together. Not the easiest thing to do when supporting users in multiple time zones and locations. This is compounded even further when working from inventory data that is incomplete or out of date.
Software Inventory plays an even more critical role in large enterprises and companies demand data that can be verifiably trusted. Critical decisions and plans are made from software inventory data. Working off stale, incomplete, and inaccurate data seriously impacts a company's ability to focus on its core objectives.




