Let's say you have a need to find out which machines have a particular file on a disk.
Maybe some secret file has broken containment in the office and you need to track down the copies and destroy them, or, perhaps, maybe discover which machines have been compromised by a virus that generates filenames of unknown form.
In the case of a virus, you may need to be able to find a filename and delete them pretty darn quick.
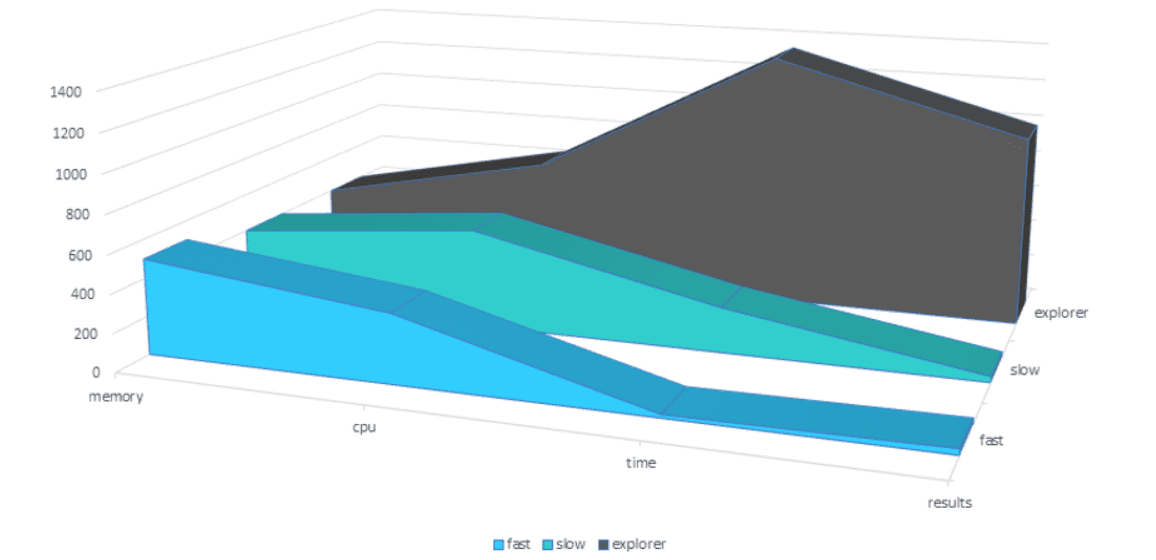
Imagine having to use Windows Explorer or a WMI query to do this—adding in the curveball that it’s company policy to turn off the Windows Indexing Service because it so intrusive and resource hungry, usually interrupting your users at the worst of times. Unless you target one drive at a time, Explorer will search all the attached network drives across your estate. This would cause a denial of service attack on your already stressed shared drive servers.
That makes the task impossible to perform in a short timescale for your whole estate. (Maybe a scripting guru could do it in the medium term and be ready for next time you need to do it.)
If you have Tachyon deployed, however, the task is trivial and can take just a few seconds for most machines to report back.
Even your biggest machines will take (literally) a minute or so to complete the task— meaning within a few minutes, you will have some feel for your exposure to the problem at hand. This compares to Explorer taking more than 22 minutes to perform the same task and will then leave you with a secondary task to perform— filtering the results for each machine. That is if you could even gather them all together in one place. Lets not talk about the WMI query time!
The Tachyon Agent is designed to have minimal resource impact on the local machine that it is deployed to, as well as not causing any potential denial of service side effects within your organization.
Below is a graph showing relativistic comparisons of the various methods we have measured for the scenario of finding a specific filename across the physically attached disks on a power user’s Windows PC. The time measured is the execution time at the agent[1].
The task measured was finding an exact filename of ‘test.txt’ on the physical hard disks. Only the two Tachyon methods restrict the search to the local physical hard disks.
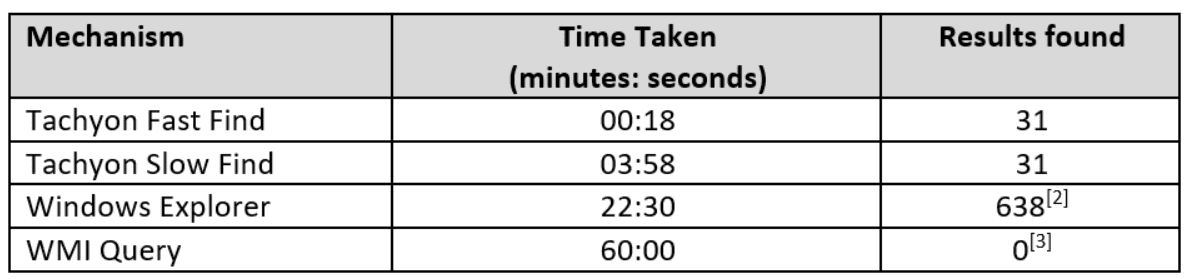
From a resource usage perspective, the fast method uses slightly more memory and CPU than the slow method for the very short period that it runs for.
The total time to discover exposure across the estate would depend on the size and various parameters within Tachyon as to how quickly the agents all perform the instruction, as by default some staggering of execution would occur with a particular configurable window, however it can be configured the agents could all be set to execute the instruction immediately upon receipt.
Explorer will by default return filenames that bare any vague resemblance to the non-wildcard search criteria.
the WMI Query took way too long and no results were given within the hour we tolerated waiting for it to finish.
For more information on Tachyon, check out our playlist on YouTube or get in touch with a specialist.



