No. You're not. Because they don't exist.
I’ve been working in various areas of IT for over 20 years. Inventory, Security, SAM… in each field I’ve always said that there’s no “silver bullet” – there’s no one tool that can do everything.
That’s still true, but working with Tachyon over the past several months I’ve been amazed by its flexibility and power. Send instructions to literally ALL of your endpoints (up to 1.5 million of them!) to gather data or take actions for almost any purpose.
I’ve been working with customers helping them use Tachyon to full effect – we’ve done things like:
For IT Security:
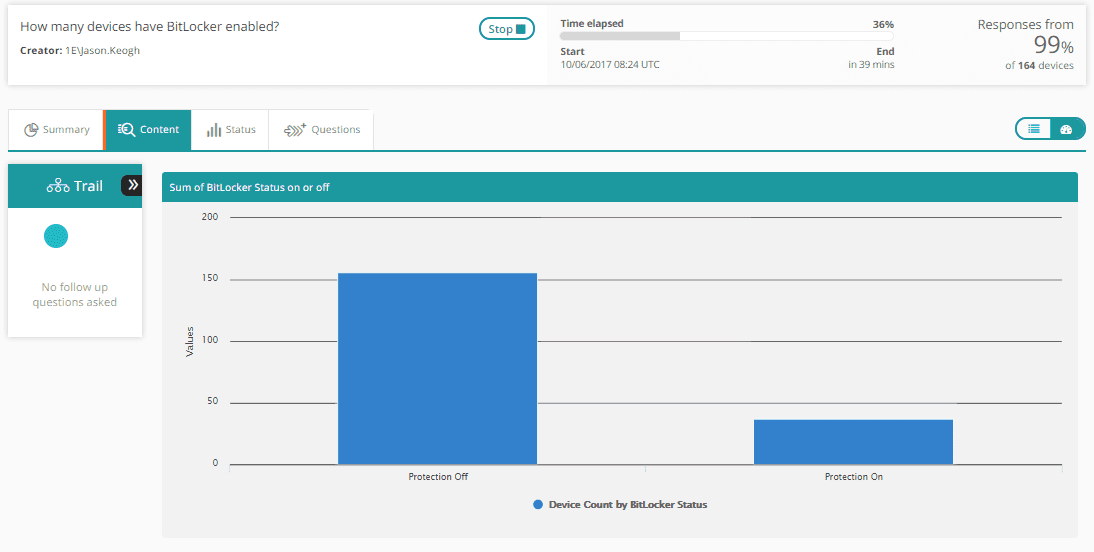
Check BitLocker status across all Windows machines. Enable it where it is disabled.
Cloud-based software usage analysis:
Check usage of SaaS applications – measure usage of Cloud apps. This single product pack is the equivalent of a “killer app” for companies using cloud-based software – and let’s face it, which companies are NOT using Salesforce, HubSpot, GoToMeeting, WebEx, etc.
The level of spending on Cloud apps is immense – but the effort to understand and visualize usage is huge. A single enterprise might have dozens of cloud service providers each with at least one, often several, management consoles… to consolidate user data across them, even to log in to them all is a significant effort. Tachyon starts with the endpoint, not the server – so it doesn’t matter. Usage is counted on each endpoint and consolidated and graphed across multiple cloud-based services (and you can edit the list to add more providers easily!).
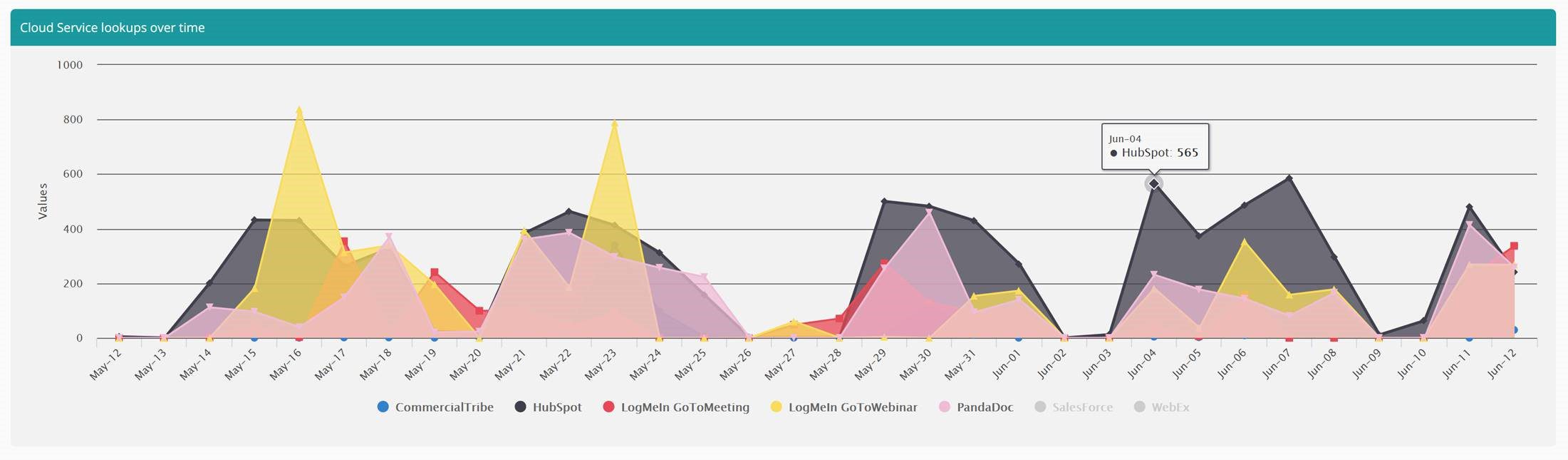
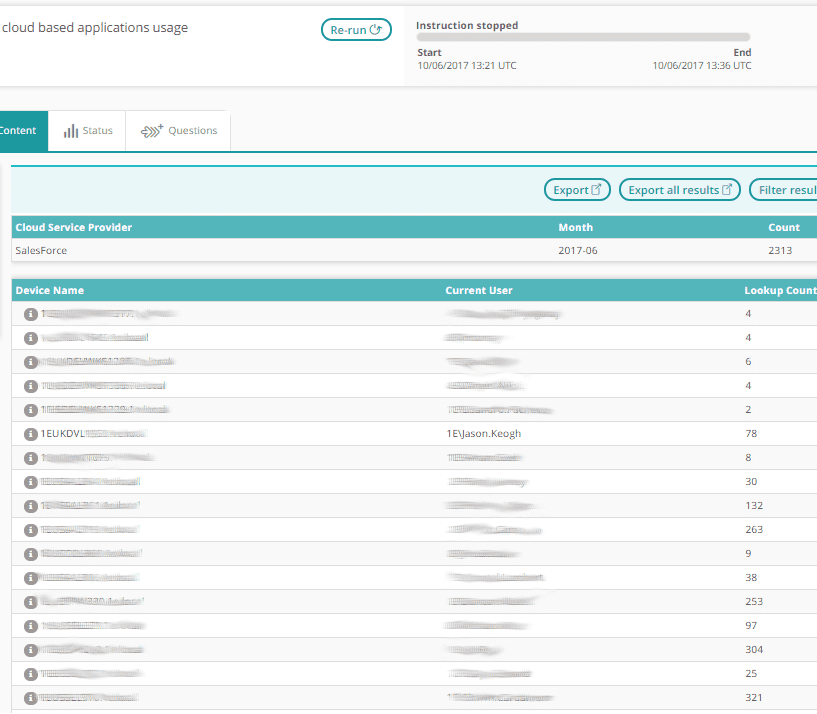
This can provide graphs of usage over time (as shown above) and details of users who have used specific Cloud apps in a given month. From the data below, we can see my usage of Salesforce on my machine and compare that to other users:
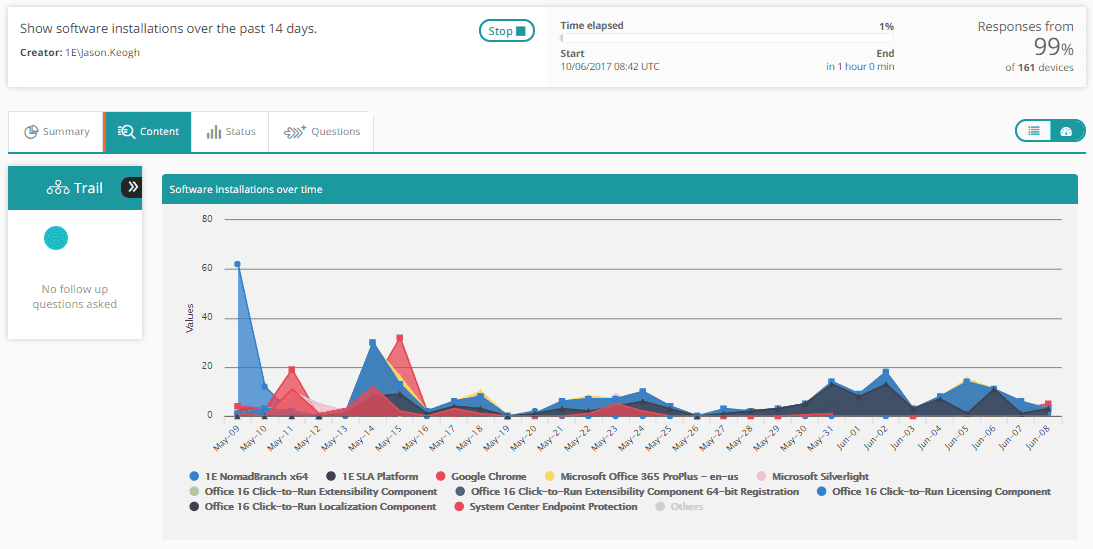
Monitoring and measuring installation of software over time:
Again, we can graph this, but also present low-level details of which machine, what software, when.
These are just some small examples of things which can be enabled with Tachyon. Note that each of these functions are enabled using Product Packs. IT Ops and IT Security Tachyon Administrators can write their own Product Packs, leveraging the Tachyon SCALE language. (Simple Cross-platform Agent Language for Extensibility).
As suggested in the name, SCALE is cross platform, meaning many extension can be written just once and work across Windows, Unix, Linux and Mac endpoints. Other functions (like the Bitlocker example above) leverage native OS commands – Tachyon instructions can literally execute any command on an endpoint, assuming the instruction has been deployed to the Tachyon Server by someone with sufficient privileges to do so.
Role-based access control can see to it that only users in groups assigned to specific roles can run specific instructions in specific Product Packs… the level of control matches the level of power available.
Tachyon is literally a query anything, do anything machine, from an endpoint perspective. It isn’t a silver bullet though.
- Tachyon can tell you about what software is installed when, where, and by who but it can’t tell you about your software license entitlements (although 1E AppClarity can do that…)
- Tachyon can instruct machines to download and execute a specific package, and while it has functions built in to minimize the negative impact on the network, it doesn’t go so far as to monitor network traffic proactively to ensure business traffic is prioritized – it integrates with 1E Nomad, which does that.
- Tachyon can add a specific user to a local admin group for a period of time, but it can’t allow users to self-service request permission changes and automate approval workflows (1E Shopping can do that)
- Tachyon can search for IoC’s and list machines which have applications with known vulnerabilities (CVE’s) on them – but it doesn’t provide the CVE List or IoC feed – we are building partnerships with a number of companies in those spaces
In 1E we have a broad spectrum of Software Lifecycle Automation functions in our native tools – and we are expanding capabilities by integrating with more and more market leaders in data visualization, alerting, process control, security feeds, etc. Tachyon has power and speed – other tools can help users drive value. Tachyon is entirely driven by secure API’s, meaning integration capabilities were part of the architecture from day 1.
Tachyon isn’t a silver bullet – but it’s the most powerful IT Operations and IT Security tool I’ve ever seen or worked with and I’m really proud to be part of the team in 1E bringing this tool to market.




