“Follina,”as reported in Techcrunch and elsewhere ticks all the wrong boxes and impacts 41 Microsoft products including Windows 11 and Office 365. Huntress research even identified a way to have this execute without the user even having to CLICK anything (hovering over the icon can trigger the exploit!).
The good news is that although there is no official patch – Microsoft have issued an advisory which includes information on a registry key you can delete, to mitigate the risk.
The better news is that, if you are a 1E customer, you can implement that advice with ease, on any/all of your devices, immediately.
Download this instruction:
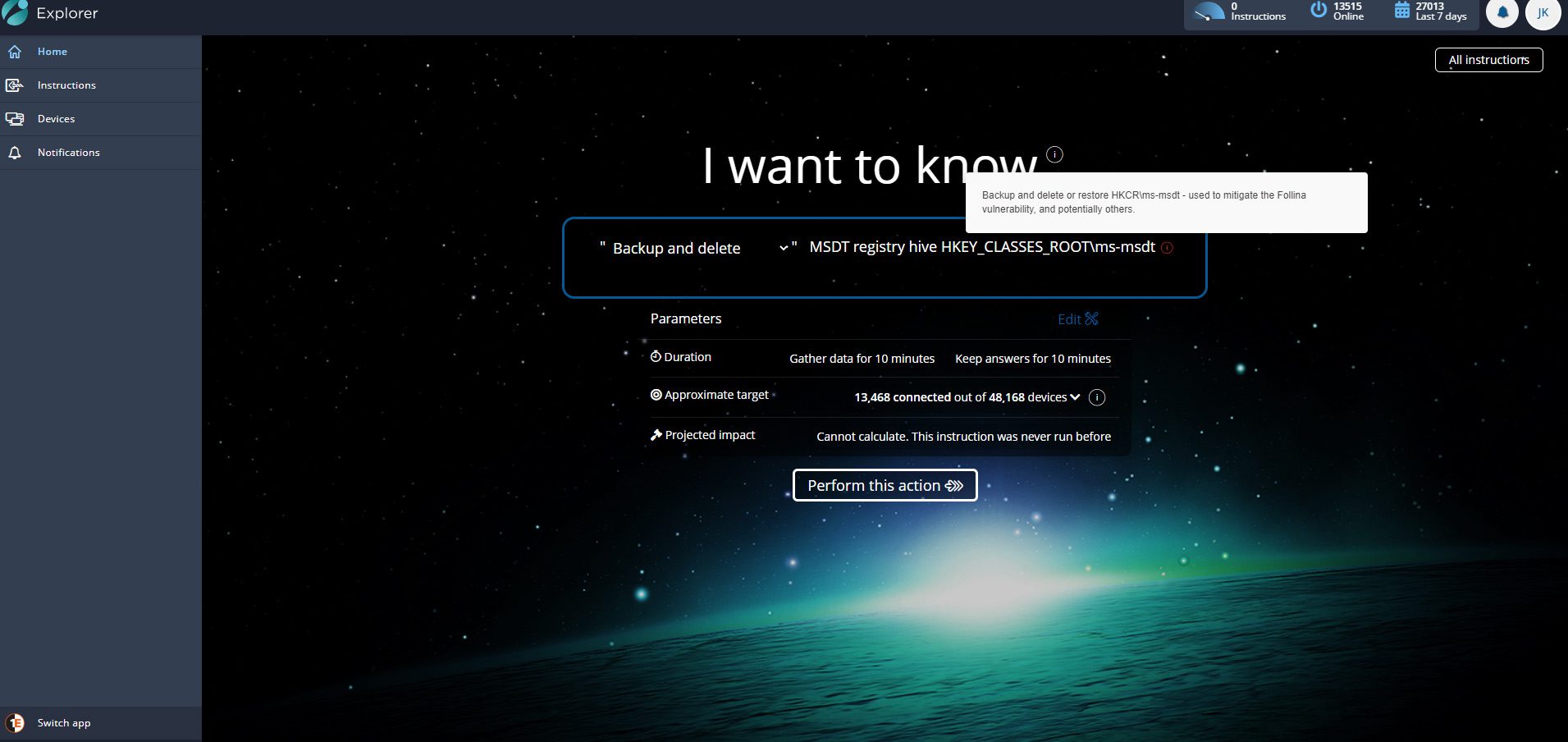
That’s it. Problem solved. Risk averted.
The instruction follows the exact Microsoft advice, running a command to back up the reg keys first – so they can be imported later. Another option allows you to restore the same keys if desired.
This was written in minutes with TIMS (Tachyon Instruction Management Studio), using the Tachyon Method NativeServices.RunCommand() and the in-built Registry functions.
This Follina attack is an example of one of many “Living off the land” type exploits which uses PowerShell or other “on-box” tools to perform nefarious tasks for the attacker.
Even without this specific instruction, you could use the existing instructions to delete a named Registry Key if immediate response is required.
With 1E you can apply the fix to all endpoints in milliseconds and then move on with your day.




