Patch Tuesday from Microsoft and other vendors is all dependent upon several underlying processes contained within the Windows operating system. In this edition of Tachyon Tuesday, we will outline each layer of this technological Matryoshka Doll, with the aim of providing tangible improvements at each layer to achieve the very visible outcome of fast, easy, repeatable patch compliance.
Layer 1 – Visibility?
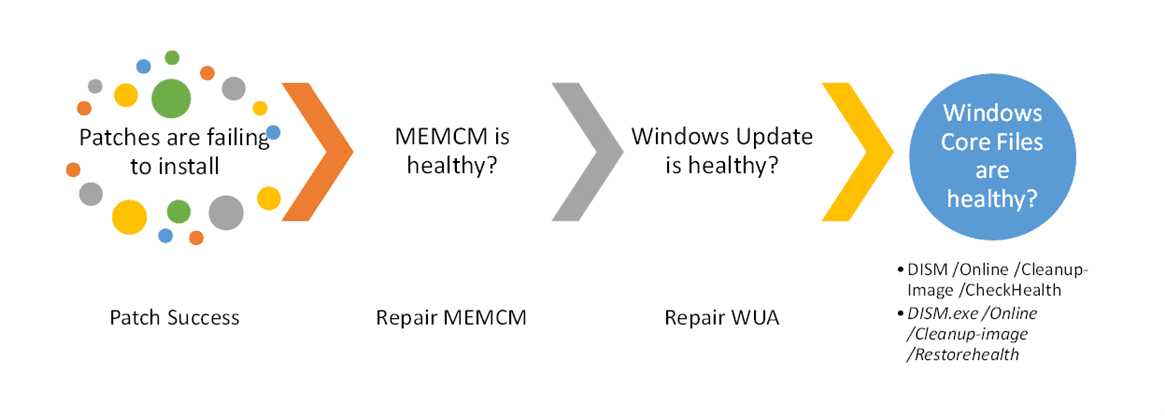
How do I know the current status of my defined windows patches?- 1E Patch Success – Automated patch management and reporting.
- Immediate visibility of patch status: Intuitive dashboards provide immediate insight into patch status, including the latest patch updates, which patches are most critical, and which endpoints require immediate patching. This data is aggregated into a patch health score to provide holistic visibility of your organization’s IT hygiene.
- Deep integration with the Tachyon Platform: Get up-to-date and accurate information about endpoint health. Tachyon’s lightweight architecture empowers IT to quickly identify vulnerabilities without network and end-user disruption and issue command and perform follow-up actions in real time.
- Drill down into telemetry: Drill down into specific patches and get details on which devices are missing high-priority or critical patches. IT can quickly identify how many devices are vulnerable, discover which patches have been deployed to all or groups of endpoints, and determine the severity and vulnerability of patches.
Layer 2 – Patching Source?
If you are using Microsoft Configuration Manager (MEMCM or SCCM) you probably already have Automatic Deployment Rules (ADR) rules in place. Those only work as well as the CM client. 1E has extensive and deep experience making CM absolutely sing. The guaranteed State MEMCM Client Health – Tachyon Exchange (1e.com) ensures the health of another 7% (on average) of persistently broken devices.
Layer 3 – Windows Update Healthy?
Once the data is transferred to your device from Windows Cloud, MEMCM, or a local WSUS server, the local Windows Update Agent (WUA) can still be broken. The detailed steps in this Microsoft Docs article Windows Update – Additional resources – Windows Deployment | Microsoft Docs will fix the issue for a while on a single device. 1E has provided an easy-to-use Guaranteed State that will both check the health of WUA and – if required – repair it, following the steps in this document.
Layer 4 – Windows Core files Healthy?
Windows core files are frequently patched and updated by, well, patching. However, as we have all experienced, a device can become out of compliance. The number one response in the forums for an unhealthy windows client is to run SFC /SCANNOW. System File Checker (SFC) is a legacy command line that looks at the registered files of the Windows operating system. This implies the correct files, are correctly registered, and correct versions exist. Every step of this process is fraught with potential mismatches and issues – Exactly the symptoms we are all seeing.
How do we fix this issue?
Ironically, for Windows 10 a replacement for SFC exists. Deployment Image Servicing and Management (DISM). This tool is for windows administrators to prepare, modify, restore, and repair system images including Setup, Recovery Environment, and WinPE. Neat! What commands do I need to run to make this all go away?
Three Step Process
CheckHealth
- Will report on any known damages or corruptions but won't fix anything.
- DISM /Online /Cleanup-Image /CheckHealth
- This will report the results of the last time a ScanHealth step was run. Think quick reporting on what the OS knows about itself.
ScanHealth
- DISM /Online /Cleanup-Image /ScanHealth
- A scan that will check issues and update the CheckHealth status results.
- This process may take a few minutes.
RestoreHealth
- DISM /Online /Cleanup-Image /RestoreHealth
- This is the step to run that will make everything work better!
WARNING: If this step is so great why doesn't everyone run it every day? Simple; this will cause the local device to reach out to the internet – specifically Microsoft Update Catalog. Depending on the version and patching the client will download the full OS (3 to 6 gb). This is (might have changed) straight SMB.
How do you prevent going to the internet? Well that is going to require a WIM file that is locally available.
DISM /Online /Cleanup-Image /RestoreHealth /source:C:\Sources\Install.wim:1 /LimitAccess
/Source = local or network file location of a WIM and the : Colon is the index in the image that refers to the matching OS on the device.
/LimitAccess = don't go out to the internet
How do we know which WIM to use? Again, MEMCM to the rescue for Enterprises. You can easily precache out at a low priority the WIM file with 1E Nomad. Nomad Content Distribution from 1E – Windows Software Deployment
If you found this Tachyon Tuesday blog helpful, why not check out the Masterclass session Jason delivered at the Work From Anywhere conference earlier this year? Or subscribe to our YouTube channel to stay up to date with the latest Tachyon Tuesday vlog content!




